For many IT and security leaders in 2026, the challenge isn’t a lack of tools, it’s the overwhelming amount of data those tools generate. As AI-powered attacks become faster and more evasive, the mid-market is moving away from fragmented protection and toward integrated defense models.
To make the right investment for your organization, you need to look past the marketing labels and understand the operational reality of each approach.
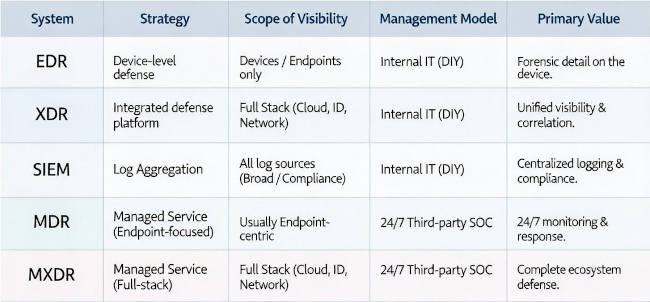
EDR: The Foundation of Modern Visibility
Endpoint Detection and Response (EDR) is the evolution of traditional antivirus. While legacy AV looked for “known bad” files, EDR looks for “bad behavior” and provides a centralized platform for security teams to monitor and investigate threats across all devices.- How it works: agents are installed on your laptops, servers, and mobile devices. These agents record every process, script, and network connection. If a user downloads a seemingly benign file that suddenly starts trying to modify system registry keys, the EDR flags it.
- The Difference: EDR provides deep, surgical visibility into what is happening on a specific device. It allows you to “roll back” an attack to a safe state and provides the forensic data needed to understand how a breach started. It also gives administrators a single console for monitoring and management, which legacy AV lacks.
- The 2026 Reality: EDR is no longer optional, it is the baseline. However, its scope is limited to the device. If an attacker steals a password and logs into your cloud environment directly, EDR is blind to that movement.
XDR: Breaking the Silos
Extended Detection and Response (XDR) was born from a simple realization: attacks don’t stay on one device. They move from an email to a laptop, then into your cloud infrastructure, and finally toward your sensitive data.- How it works: XDR isn’t just a bigger EDR; it’s an integration layer. It pulls in telemetry from your network firewalls, email gateways, cloud workloads (AWS/Azure), and identity providers.
- The Difference: The “X” stands for Extended. It correlates data across these domains. For example, XDR can see that a suspicious login from a new country (Identity) is linked to a PowerShell script running on a server (Endpoint).
- The 2026 Reality: XDR reduces “alert fatigue” by combining multiple alerts into one incident. It is the architectural choice for organizations that want to see the whole battlefield, not just individual foxholes.
SIEM: The Central Log Collector
Security Information and Event Management (SIEM) is a complementary technology focused on collecting, storing, and analyzing log data from virtually any source across the IT environment.- How it works: SIEM ingests logs from infrastructure devices, applications, and often complements EDR/XDR data. It is crucial for getting visibility into devices that cannot accept an agent, such as legacy hardware, network switches, or specialized appliances.
- The Difference: SIEM provides broad, compliance-focused data aggregation, while EDR/XDR are typically focused on threat detection and response actions. In many solutions, SIEM exists separately, requiring security teams to pivot between multiple consoles to correlate logs with device activity.
- The 2026 Reality: A SIEM is essential for comprehensive compliance and forensic logging, but without integration into EDR/XDR systems, it can create operational silos. The most effective solutions offer tightly integrated EDR, XDR, and SIEM capabilities within a single pane of glass.
MDR: Managed Expertise for Stretched Teams
The biggest challenge for mid-market firms isn’t the software—it’s the people. Managed Detection and Response (MDR) is a service that provides you with a 24/7 Security Operations Center (SOC).- How it works: You deploy EDR or XDR technology, but a third-party team of experts monitors it around the clock. They triage every alert, hunt for hidden threats, and often take immediate action to contain a breach on your behalf.
- The Difference: MDR is a service, not just a tool. It fills the “skills gap” by giving you access to elite analysts without the high annual cost of building a 24/7 internal team. The critical distinction is that standard MDR is often heavily focused on the Endpoint (EDR) layer of defense.
- The 2026 Reality: For many SMBs, MDR is the most cost-effective way to meet cyber insurance requirements and ensure someone is watching the gate while the IT team is focused on business operations.
MXDR: The Gold Standard of Defense
Managed Extended Detection and Response (MXDR) represents the pinnacle of modern security. It combines the broad, cross-stack visibility of XDR with the 24/7 human expertise of MDR.- How it works: MXDR providers manage your entire security ecosystem, aggregating cloud, identity, network, and endpoints. They use AI-driven automation to correlate data across your stack while expert hunters look for the sophisticated “low and slow” attacks that automated tools might miss.
- The Difference: While standard MDR typically offers monitored EDR, MXDR offers full-stack defense based on XDR architecture. It ensures that your cloud environment, identity provider, and network are just as guarded as your CEO’s laptop.
- The 2026 Reality: As organizations become “cloud-first,” MXDR has become the necessary standard for preventing business-halting breaches in complex, distributed environments.