In today’s digital landscape, staying one step ahead of cyber threats is a necessity, not a luxury. We make it affordable.
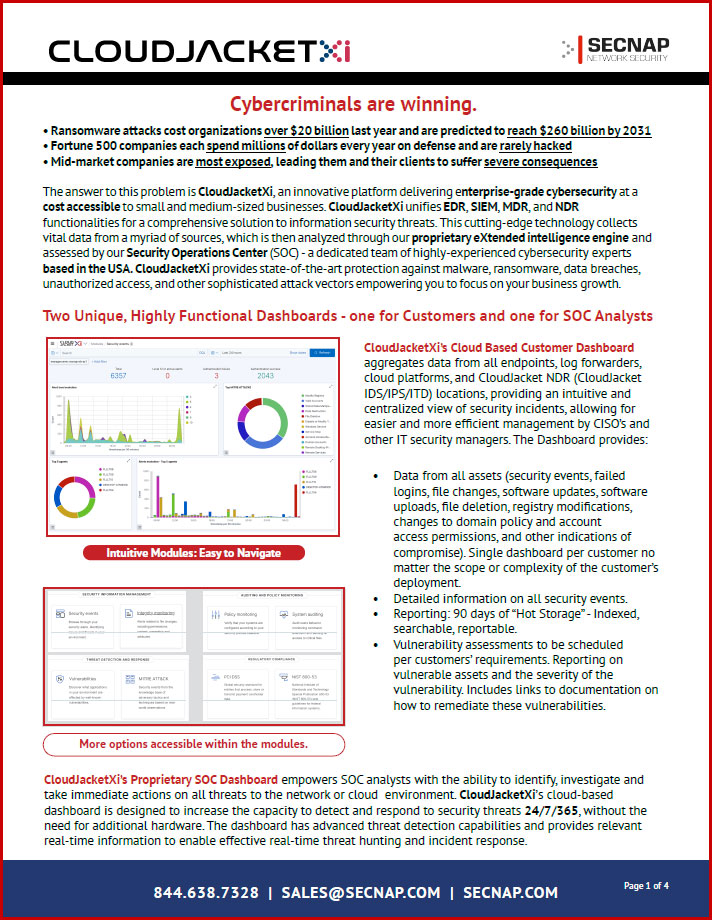
Built for the unique needs of SMBs to mid-market enterprises, our platform provides an all-encompassing, multifaceted cybersecurity solution that matches the robust defenses used by Fortune 500 companies. CloudJacketXi, a unified threat intelligence platform, delivers a comprehensive solution to information security threats. This cutting-edge technology collects vital data from a myriad of sources, which is then analyzed through our proprietary eXtended intelligence engine and assessed by our Security Operations Center (SOC) – a dedicated team of highly-experienced cybersecurity experts based in the USA. CloudJacketXi provides state-of-the-art protection against malware, ransomware, data breaches, unauthorized access, and other sophisticated attack vectors. With us, you get an unparalleled blend of protection, detection, and response capabilities, all bundled into one powerful package. Our value lies not just in our defense system, but in the peace of mind we provide, allowing you to focus solely on driving your business to new heights.

Self Monitored
CloudJacketXi Basic
From
$10
/user/month
- CloudJacket Xi Platform
- Client accessible Web Portal
- 3 Hours of Technical Support included monthly
- Self Monitored
- Data Collection & Analysis
- 90-days Data Retention Period
- Endpoint Agent provisioning
- System File Integrity Monitoring
- Malware Detection
- Antivirus Monitoring
- Endpoint Inventory
- 10% Discount on other SECNAP security services.
SOC Monitored 24/7/365
CloudJacketXi Standard
From
$30
/user/month
- CloudJacket Xi Platform
- Client accessible Web Portal
- 24/7/365 Professional Support and Maintenance
- SECNAP Security Operations Center
- Data Collection & Analysis
- 90-days Data Retention Period
- Endpoint Agent provisioning
- System File Integrity Monitoring
- Malware Detection
- Antivirus Monitoring
- Endpoint Inventory
- Vulnerability Detector
- Compliance Reporting
- Security Configuration Assessment
- 20% Discount on other SECNAP security services.
SOC Monitored 24/7/365
CloudJacketXi Premium
From
$50
/user/month
- CloudJacket Xi Platform
- Client accessible Web Portal
- 24/7/365 Professional Support and Maintenance
- SECNAP Security Operations Center
- Data Collection & Analysis
- 365-days Data Retention Period
- Endpoint Agent provisioning
- System File Integrity Monitoring
- Malware Detection
- Antivirus Monitoring
- Endpoint Inventory
- Vulnerability Detector
- Compliance Reporting
- Security Configuration Assessment
- Syslog Receiver (3 sources included)
- Cloud Platform Monitoring (One Cloud Platform included)
- Active Response
- 30% Discount on other SECNAP security services.

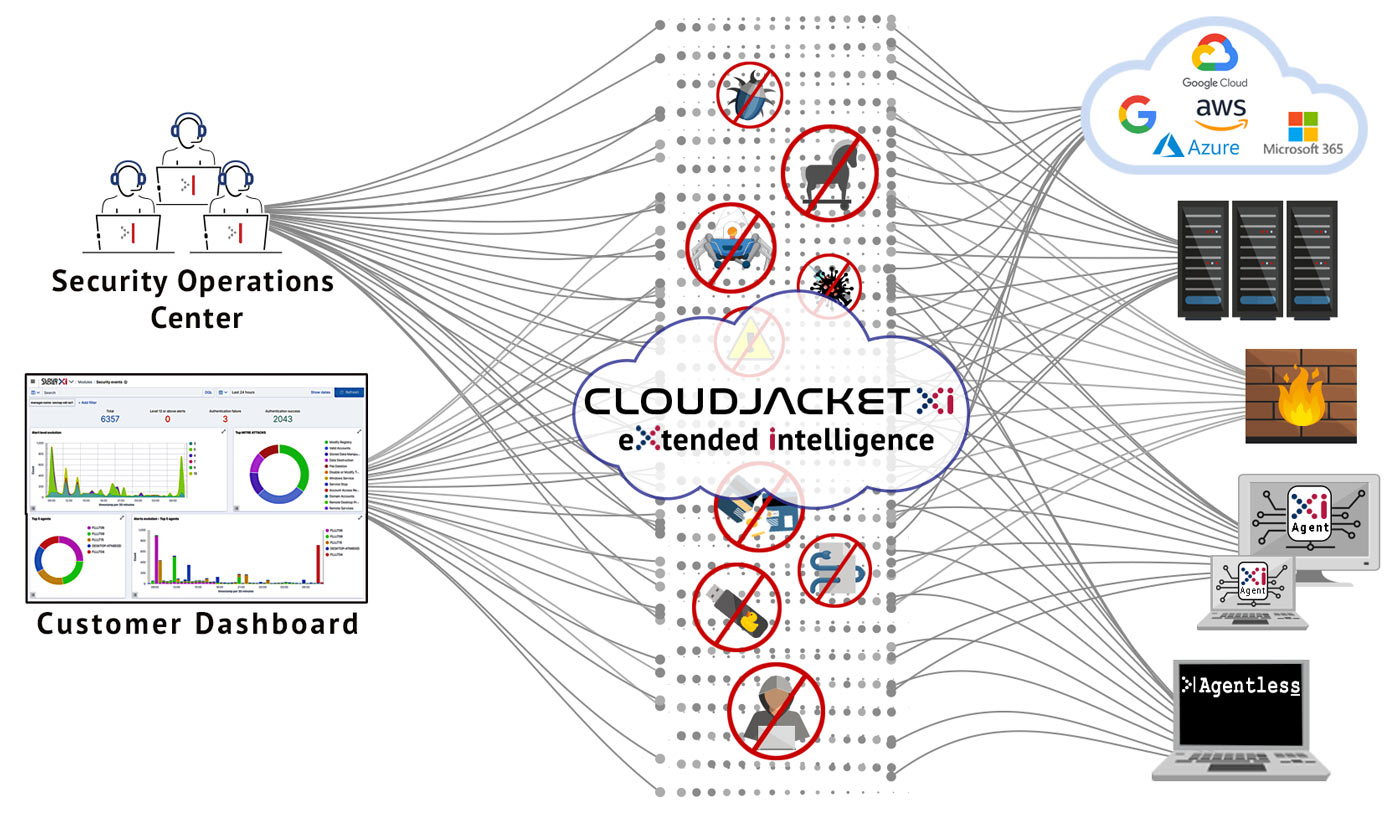
Using both software agents (lightweight and multi-purpose, installed on endpoints such as laptops, desktops, servers, cloud instances, and virtual machines) and agentless monitoring (for firewalls, switches, routers, etc.), CloudJacketXi’s eXtended intelligence engine collects data from all key sources in a network or cloud implementation, uses our proprietary software to analyze and correlate the data to accurately parse through the millions of potential threats and behavioral anomalies that occur daily in a network or cloud, identifying those that are real threats, and presenting these threats to our U.S.-based SOC analysts for final analysis via our proprietary security operations centers’ dashboard.
Features & Add-Ons
* Denotes the feature requires an endpoint agent to operate.
** Denotes the feature requires deployment of NDR to operate.
CloudJacket Xi Platform
A SECNAP managed, cloud-delivered cybersecurity platform that collects, aggregates, indexes, analyzes and presents data via a Web Portal. Provides an in-depth overview of a client’s security landscape, displaying all activity and trends within the past 90 days for security information and event management.
Web Portal
A cloud delivered web service that allows authorized Client staff to access and view data collected by the CloudJacketXi Platform. Users with access to the Web Portal are able to generate reports and create custom visualizations and dashboards.
Technical Support
Includes configuration support, troubleshooting of issues encountered, user account management, and retained data retrieval for the CloudJacketXi Platform. Does not include Professional Support for security related issues or training.
Professional Support
Includes Technical Support & Maintenance as well as support for questions relating to security events on the CloudJacketXi Platform.
SECNAP Security Operations Center (SOC)
A team dedicated to continuously monitor, evaluate, and respond to security alerts generated by the CloudJacketXi Platform’s eXtended intelligence Engine. Utilizes proprietary technologies, tactics, techniques, and procedures to proactively seek out and identify potential security threats. Coordinates appropriate incident response actions to protect the confidentiality, integrity, and availability of data.
Data Collection & Analysis
Collects and analyzes data received by the CloudJacketXi Platform from endpoint agents, syslog receivers, docker containers, cloud platforms, and sensors.
Data Retention Period
Length of time in which data (e.g. logs, events, alerts) received or generated by the CloudJacketXi Platform is retained and stored in a secure and verifiable compressed format.
Endpoint Agent Provisioning
Refers to the process of providing software agents and instructions for deployment on endpoint devices within an organization’s environment. Supported Operating Systems include Windows, MacOS, Debian, Ubuntu, Red Hat, Solaris, AIX, and HP-UX. Agents communicate with the CloudJacketXi Platform through an encrypted and authenticated channel. The configuration, distribution, and activation of these agents on the client’s systems is required for numerous CloudJacketXi features as denoted with an * below.
System File Integrity Monitoring*
Intermittently scans and monitors the Modifications, Additions, Deletions, Permissions, Contents, Ownership, and Attributes of system files and registries.
Malware Detection*
Scans filesystem and registries for malicious files. Detects rootkits by checking running processes, hidden ports, unusual files, unusual file permissions, hidden files, and network interfaces.
Antivirus Monitoring*
Monitors specific antivirus software (Windows Defender, ClamAV) for events including antivirus status, actions, definition updates, scans, and alerts of potential malware.
Endpoint Inventory*
Displays endpoint system information including basic Hardware Information, Operating System information, Installed Packages, Running Processes, Network Information (Settings, Interfaces, Ports), and Windows updates.
Vulnerability Detector*
Scans for vulnerabilities in the operating system and applications installed on endpoints. Utilizes external vulnerability feeds updated by Canonical, Debian, Red Hat, Arch Linux, Amazon Linux Advisories Security (ALAS), Microsoft, and the National Vulnerability Database (NVD). Displays the Common Vulnerabilities and Exposures (CVE) ID numbers, Affected Package names, Severities, as well as Remediation Status.
Security Configuration Assessment (SCA)*
Periodically checks and compares the current configuration of supported Operating Systems or Services against Benchmarks primarily developed by the Center for Internet Security (CIS). These checks offer practical guidance for hardening Operating Systems and Services against known security weaknesses.
Available Operating System CIS Benchmarks:
- CIS Benchmark for Windows 2012 R2
- CIS Benchmarks for Windows versions 10 and 11 Enterprise
- CIS Benchmarks for Windows Server versions 2016, 2019 RTM, and 2022
- CIS Benchmarks for Debian/Linux versions 7 through 10
- CIS Benchmarks for Ubuntu Linux versions 14.04, 16.04, 18.04, 20.04, and 22.04 LTS
- CIS Benchmarks for Red Hat Enterprise Linux versions 5 through 9
- CIS Benchmarks for CentOS versions 6 through 8
- CIS Benchmarks for SUSE Linux Enterprise 11 and 12
- CIS Benchmark for SUSE SLES 15
- CIS Benchmarks for Amazon Linux versions 1 and 2
- CIS Benchmarks for Oracle Solaris versions 11 and 11.4
- CIS Benchmarks for Apple macOS versions 10.11, 10.12, 10.13, 10.14, 10.15, 11, 12, and 13
Available Service CIS Benchmarks:
- CIS Benchmark for Apache HTTP Server 2.4
- CIS Benchmark for Oracle MySQL Community Server 5.6
- CIS Benchmark for Oracle MySQL Enterprise 5.6
CIS Benchmarks for Microsoft SQL Server versions 2012, 2014, 2016, 2017, and 2019
- CIS Benchmark for Microsoft IIS 10
- CIS Benchmark for MongoDB 3.6
- CIS Benchmark for NGINX 1.14.0
- CIS Benchmark for Oracle Database 19c
- CIS Benchmark for PostgreSQL 13
General SCA Benchmarks:
- Benchmark for Windows auditing
- Benchmark for Linux auditing
- System audit for web-related vulnerabilities
Compliance Reporting*
Associates event/alert data with defined regulatory compliance requirements within the following regulatory standards:
- Payment Card Industry Data Security Standard (PCI DSS)
- National Institute of Standards and Technology 800-53 (NIST 800-53)
- Trust Services Criteria (TSC)
- General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability (HIPAA)
Active Response*
Refers to proactive actions taken manually and/or automatically in response to threats when an endpoint is suspected of being compromised. Involves actions to terminate or disrupt communications on endpoints with indicators of compromise deemed critical.
Docker Monitoring*
Enables the Docker listener dashboard which displays the activity and events related to Docker Images, Containers, and Networks from Docker servers.
Syslog Receiver
Collects TLS-encrypted syslog traffic from capable sources (e.g., network equipment, information systems) on the CloudJacketXi Platform. Event data is transmitted to, analyzed by, and displayed on the CloudJacketXi Platform.
Cloud Platform Monitoring
Collects data from the following Cloud Platforms:
- Amazon Web Services (AWS)
- Microsoft Azure (Including Active Directory)
- Office 365
- Google Cloud Platform (GCP)
- GitHub
Event data is transmitted to, analyzed by, and displayed on the CloudJacketXi Platform.
MITRE ATT&CK Module
Correlates events on the CloudJacketXi Platform to known tactics, techniques, and procedures (TTPs) defined by the MITRE ATT&CK framework. Provides descriptions for tactics and techniques as well as associated known threat actors.
Network Detection and Response (NDR)
An Intrusion Prevention System (IPS) typically deployed in-line between a gateway and core switch. The in-line sensor performs real-time deep packet inspection to identify anomalous network activity. Traffic crossing the IPS sensor deemed to be potentially malicious is blocked. Event data is transmitted to, analyzed by, and displayed on the CloudJacketXi Platform. NDR is required for features denoted with an ** below.
Lateral Threat Detection (LTD)**
Receives data (up to 1Gbps) from a switchport configured to use Switched Port Analyzer (SPAN), also referred to as Port Mirroring, to provide additional visibility into network traffic which is not crossing an in-line IPS sensor. The LTD sensor performs deep packet inspection to identify anomalous network activity.
Internal Threat Detection (ITD)**
Utilizes deceptive security to identify potentially hostile threat actors operating inside of an internal network. The ITD sensor monitors access to simulated network services and filesystems to identify unauthorized access.
Monitored and Managed by our SOC
Our 24/7/365, U.S.-based Security Operations Center will manage and monitor your network for security breaches and respond immediately to stop threats dead in their tracks (not available with the Basic tier).
Our security analysts are a dedicated team, diligently serving as overwatch to review every alert, so that you don’t have to. Let our team keep your data safe, secure, and out of the hands of bad actors.
Let your team run the systems that operate your business. Free them from the headaches of trying to manage security as a part-time job or afterthought. Watch them shine in their role, assured that the systems they depend on are uncompromised.