External Security Assessments
Reduce Risk with External Vulnerability Assessment
The best way to stop an attacker from succeeding is to think like one. SECNAP’s security experts will assess your public facing infrastructure to uncover potential vulnerability and out-dated software. Our assessments are performed by our team of certified security experts who have extensive experience reviewing real-world exploits on a daily basis.
SECNAP’s External Assessments leverages automation in order to test against over 100,000 vulnerabilities and is complimented with manual testing to further explore gaps in your security posture. Our US-based security experts will work to identify weaknesses that could be exploited to interfere with the confidentiality, availability, and integrity of your network. With our findings, we will provide a detailed report and give your team guidance towards how to minimize your network’s external facing attack surface.
Benefits of Performing an External Vulnerability Assessments
An External Vulnerability Assessment can help justify the resources needed to close the security gaps that directly impact your risk level. With our detailed report, you will be able to facilitate the compliance process and identify potential compliance violations.
Often times your sales team can also benefit from security. For example, during the vetting process of new vendors your prospects may require a copy of your most recent vunerability assessment to ensure they are doing business with a secure company.
Assessment Report includes:
- Executive Report for the Non-Technical
- Detailed Findings and Remediations Report
- Comparison to Previous Scans if Applicable
- Screenshots of Confirmed Vulnerabilities
- Raw Data Output of Findings
%
73% of Breaches Involve External Actors.*
What happens during testing?
External Vulnerability Assessments consists of remote scans and tests generated from our Secure Operations Center (SOC) to determine if vulnerabilities can be detected on web-facing hosts. Over 100,000 automated tests are performed on external facing surfaces including network devices, web servers, firewalls, hypervisors, databases and operating systems.
During testing, our security team will manually confirm vulnerabilities in a non-intrusive manner in order to prevent disruption of critical services. Once testing is concluded, our security experts will report back on what actionable remediation should be prioritized to reduce your external attack surface.
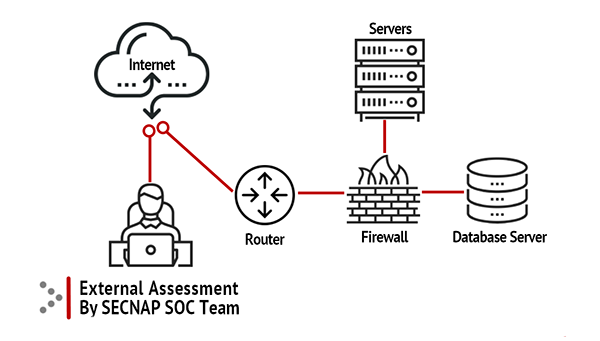
How does testing get done?
During testing our US-based security experts will run a series of automated and manual probes.
Performed Scans Include:
- Catalog all active ports/services on network
- Check for operating system vulnerabilities
- Check for web server vulnerabilities
- VoIP vulnerability testing
- Testing for malware
Manual probes may include:
- Check for external services misconfigurations
- Confirm best practice configurations for services
- Evaluation of service inherited attack vectors
- Escalate compounding low-risk vulnerabilities
- Verification of vulnerabilities detected
Frequency of Testing
Testing is a snapshot in time of your current security posture. Depending on your business vertical, it is recommended that testing be performed monthly or at least quarterly. It is particularly important after the network undergoes any significant changes as new security gaps may arise. Compliance regulated industries may require security assessments annually to ensure compliance.






