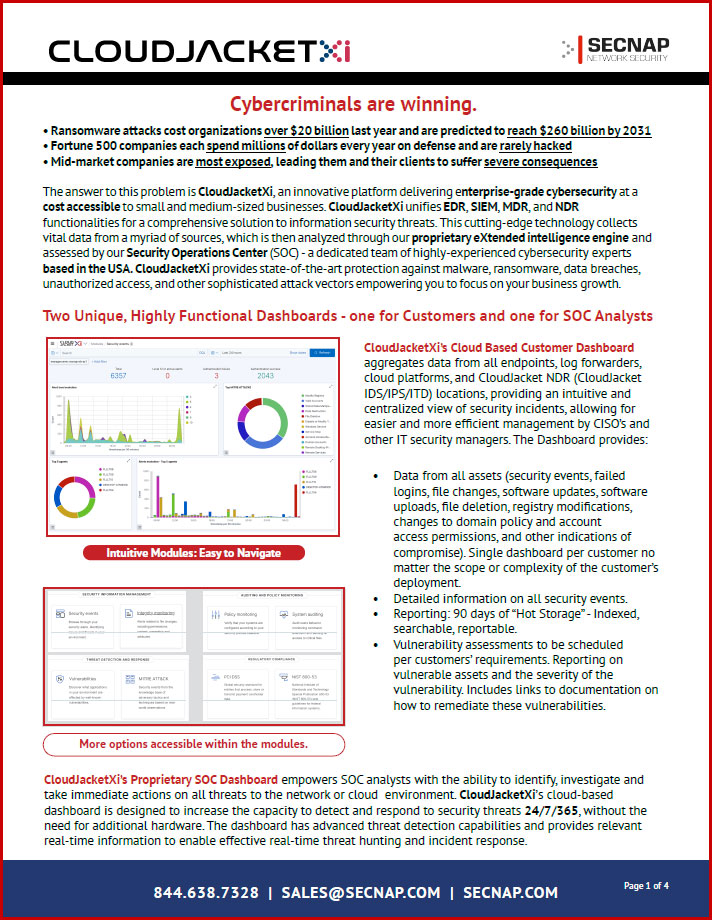
Internal Vulnerability Assessments
Mitigate Risk with Internal Vulnerability Assessments
Assess your IT risk like an insider. Vulnerabilities can arise due to misconfigured hardware, out-of-date software, or even unpatched systems.
The objective of an Internal Security Assessment is to safeguard the network’s assets that could be exploited to interfere with the confidentiality, availability, and integrity of your network. A security assessment reveals an organization’s existing IT vulnerabilities and suggests recommendations to improve its overall security posture. In simpler terms, it is an assessment that reveals the immediate threats to your IT security, and shows how to fix them to ensure that they don’t occur again.
The Security Assessment Process
Here’s what a comprehensive security assessment looks like:
-
- Step 1: Due Diligence
- Step 2: Threat Modeling
- Step 3: Application and Infrastructure Deep Dives
- Step 4: Recommendations and Action Plan
Testing performed by SECNAP follows NIST SP 800-115 Technical Guide to Information Security Testing and Assessment, OWASP Testing Guide (v4), and customized testing frameworks.
Step 1 – Due Diligence
The first step is the discovery phase. You document information about the people, processes, and technologies that affect the organization’s overall security framework. This mainly involves gathering information on:
-
- The hosting and deployment infrastructure
- Open source reconnaissance against the organization
- Full port scan covering all TCP ports and the top 1,000 UDP ports of the targets in scope
- Full vulnerability scan of the targets
Step 2 – Threat Modelling
Threat modeling is the process of understanding your cybersecurity vulnerabilities by identifying system entry points and reducing the likelihood of breaches. Various threat models help you identify threats by adopting unique perspectives. For example:
-
- Process Threat Analysis – Identification of immediate threats
- Visual, Agile, and Simple Threat – Perspective of the organization
- Elevation of privilege – Perspective of the engineer
Approaching the system from different perspectives helps understand the level of threats and the feasibility of proposed solutions.
Step 3 – Application and Infrastructure Deep Dives
The security assessment during this phase reveals not only security gaps but also opportunities to cut costs. Organizations often pay for redundant instances whose costs can sometimes pile up to thousands of dollars a month.
Step 4 – Cybersecurity Recommendations and Action Plan
In the last stage of the security assessment process, you receive recommendations and insights from all the previous steps. Ideally, this is in the form of an action plan that you can quickly put into your roadmap. Unlike a raw dump of recommendations, an action plan prioritizes the deliverables based on their feasibility and impact.
After a security assessment you will get:
-
- Tactical Plan:
What do you need to do right now to fix critical security issues and reduce unexpected costs? These are straightforward fixes to specific issues. For example, focusing remediation efforts on critical vulnerabilities or eliminating outdated software to improve efficiency. Tactical recommendations will give immediate benefits to your business. - Recommendations:
It’s great to fix gaps and put out the flames, but how can you ensure that similar mistakes don’t occur again? Strategic recommendations aim to make security an essential part of your culture.
- Tactical Plan:
%
28% of Data Breaches Involve Internal Cyber Attacks*
Assessment Report includes:
- Executive Summary for Non-Technical
- Detailed Findings and Remediations Report
- Comparison with previous assessment if Applicable
- Screenshots of Confirmed Vulnerabilities
- HTML Detailed Data and Supporting Files
The final report will accurately identify and prioritize vulnerability remediation based on criticality, threat context and vulnerability severity. Easily exploited vulnerabilities that lead to large amounts of data loss or have a potential of privilege loss should be considered as high priority.
Attack Surface Testing
Our testing is built for the modern attack surface and leverages automation in order to test against over 100,000 potential vulnerabilities and 45,000 Common Vulnerabilities and Exposures. Those test are complimented with manual testing performed by a highly experienced security professional in order to confirm and further explore gaps in your security posture.
Performed Scans include:
- Catalog all active ports/services on network
- Check for operating system vulnerabilities
- Check for web server vulnerabilities
- VoIP vulnerability testing
- Testing for malware
Manual probes may include:
- Check internal services for misconfigurations
- Confirm best practice configurations for services
- Evaluation of service inherited attack vectors
- Escalate compounding low-risk vulnerabilities
Cloud Based Assessments
SECNAP offers thorough cloud testing, the activities performed during testing (but not limited to):
-
- AWS, Azure, and Internal Network Audits
- Architecture & Configuration Reviews (IAM, EC2, S3, VPC, Route53, ect.)
- Host Audits, Web Applications Assessments, and Infrastructure-Based Assessments
- Other Testing Depending on Specific Customer Content and Size
Benefits of Regular Testing
This assessment should be used to analyze the network’s current security posture. Depending on your business vertical, security maturity and sensitivity of your data, your risk tolerance may vary. In general, it is recommended that testing be performed quarterly at minimum. It is particularly important after the network undergoes any significant changes as new security gaps may arise.
Proactive Security over Compliance
Numerous state and federal laws and regulations require assessments, of which internal vulnerability assessments are an integral part. If your business is regulated by GLBA, FINRA, NCUA, HIPAA, SOX, SSAE 18 or PCI, these assessments are critical. The FTC has stated that the identification of internal vulnerabilities is a key element in a proper security program. If a breach were to occur and legal action is being taken, assessments will be valuable when proving that reasonable measures were taken to protect and secure data.
Security teams who follow the NIST Framework understand the importance of frequently identifying vulnerabilities. Each assessment will determine the system’s deficiencies for analysis. Recurring assessments will provide trending data for evaluation. A proactive stance in security, not just in compliance, requires an ongoing process that discovers and remediates vulnerabilities.